
cd# Purpose
Explain how I find a zero-day in a wifi device.
I was working to find vulnerabilities in a web interface of a wifi device. After some time I decide to reverse the firmware ;) to have access to the code on the server.

Prerequisite
Get the firmware and extract data
The upgrade is available on the website of the manufacturer in the support>download-center page.
The upgrade file is a ZIP file. The archive contain :
What we want is in .bin file.
We are going to extract data from this .bin file with binwalk
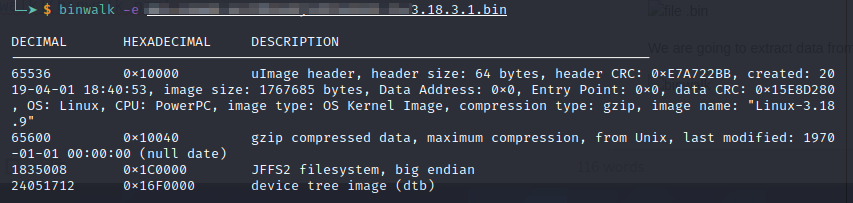
If you try the command without installing jefferson you will get an error. And you need to extract manually the .jffs2 file with the tool.
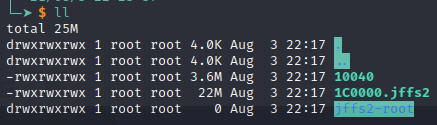
Now we have a jffs2-root folder \o/
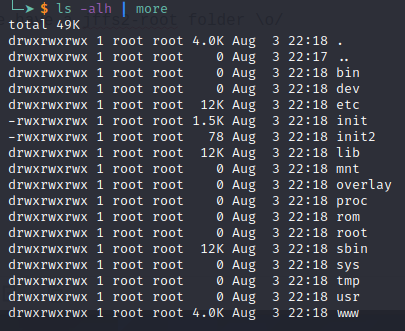
We see a linux system.
Find a vulnerability
After a long time to search, understand where files are and read LUA code … I found something interesting.
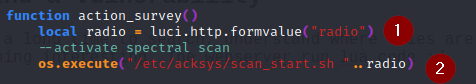
- the code grep a value from a HTTP form and put it in var radio
- the code call an internal script and concatenate it with the var radio
There is no sanitize in the radio value.
Let’s try to inject some value
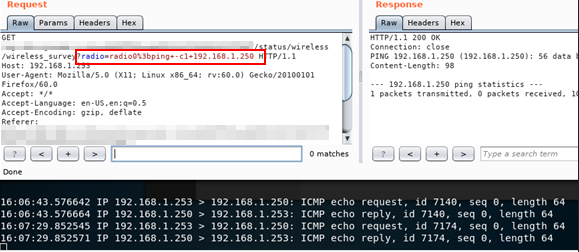
We can see that the wifi system run the Ping command \o/, we have an RCE. Next step, get a shell on busybox :)