
Informations
Websec.fr is a great website to perform PHP code review. There are ~28 challenges with different difficulty levels ;)
Captain flag
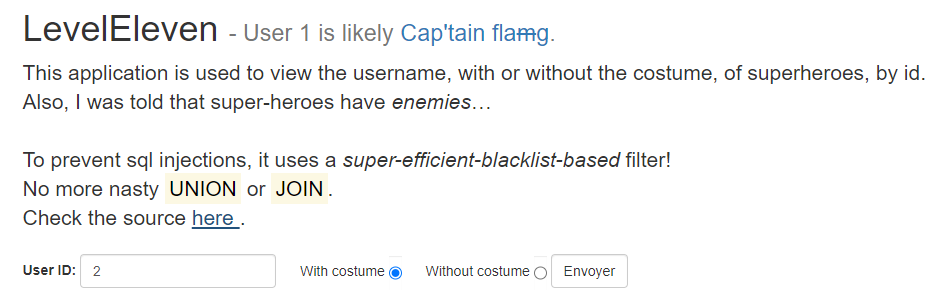
It is a form. The input is an int.
The interesting part of the code is in the ‘sanitize‘ function
1 |
|
First it check if $id is_numeric and $id>2
Second it check if the is no ‘special string’ (blacklist) in table name.
We can see that the SQL query is concatenate string and that always bad (SQLi) and it is recommended to use ‘prepared statement‘.
In CTF there’s no hazard so column ‘enemy’ is an information. We can imagine we need to find the value enemy in id 1 \o/
I do some simple test to try to inject the table value but nothing worked :/
So I try to bypass the $id with:
- big int
- 0e11111 value
- …
but nothing work :/
So I return on SQL injection tests, on table name.
It is possible to inject some query in table field in HTTP Post submit (Burp is your friend) with:
Spoiler warning
1 | user_id=2&table=(select id,username from costume)&submit=Submit |
But this don’t bypass the filter to access the id=1.
I try a time base SQLi
1 | select * from (select id,username from costume where id like 1 and substr(username,1,1) like CHAR(0X37) and randomblob(100000000) ) |
It work on sqliteonline but not on websec :/
After reading multiple post on the web I find THIS. In Sqlite ‘AS’ is not mandatory in column name alias.
1 | SELECT StudentName 'Student Name' FROM Students; |
So we can try to bypass the id column with this information and what we find before.
You can use the code SQL to generate your own Table and do some test
1 | CREATE TABLE costume (id integer primary key, username varchar(20), enemy varchar(20) ); |
Spoiler warning
1 | user_id=222&table=(select 222 id,username from costume)&submit=Envoyer |