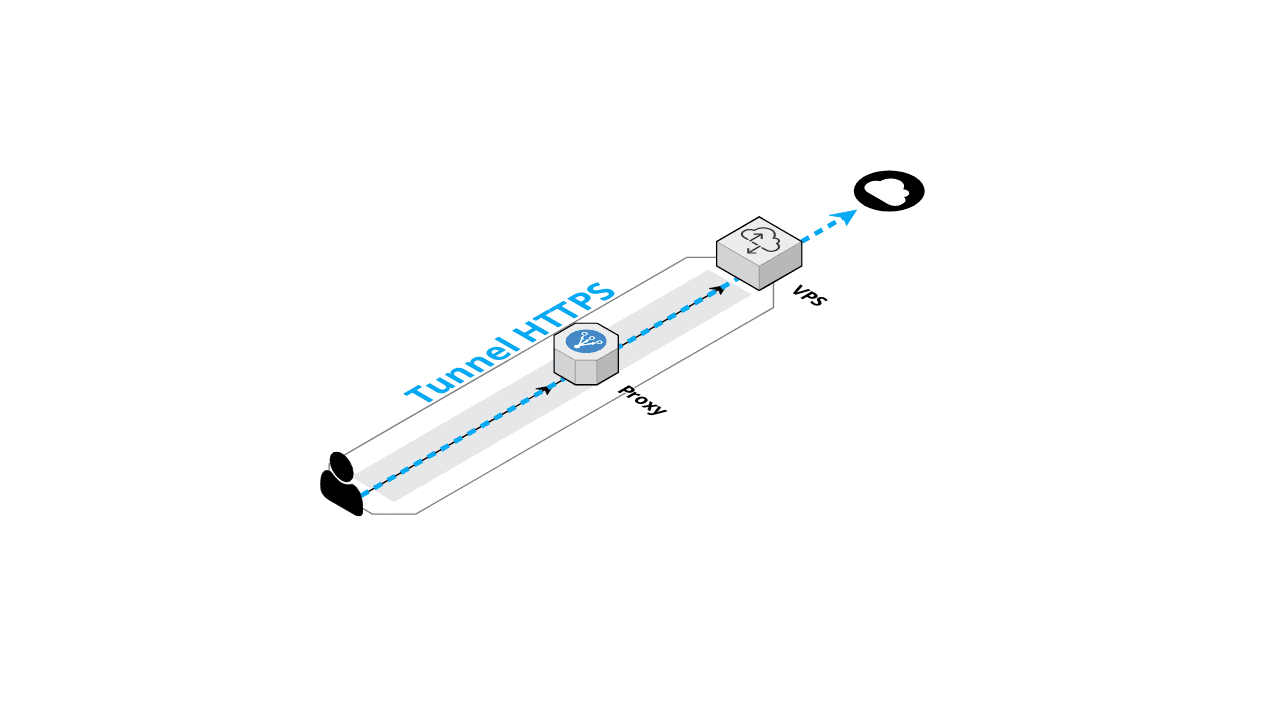
Purpose Bypass authenticated proxy by using HTTPS/TLS tunnel.
Prerequisite We need a server on Internet. A simple VPS is enough.SSF and cntlm .
SSF on both side (client and server) (linux/windows…)
cntlm on client side (linux)
Install & config Install
1 2 3 4 5 sudo apt update sudo apt install cntlm wget https://github.com/securesocketfunneling/ssf/releases/download/3.0.0/ssf-linux-x86_64-3.0.0.zip -O ssf.zip unzip ssf.zip
1 2 cntlm -H -d <domaine_AD> -u <user>
Example:
1 2 3 4 5 cntlm -H -d customerDomain.in -u user Password: PassLM FE03A594184396D6552C4BCA4AEBFB11 PassNT F3496B77FA086840D57D7F868C476AC8 PassNTLMv2 6614D6CFED66810F39A6FB6518F7AD56
Edit /etc/cntlm.conf, paste the code (at the right place) and set the IP:port of the proxy.
Start proxy
1 sudo service cntlm start
By default cntlm listen on 127.0.0.1:3128.
To use ssf you need to generate some files.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 #!/bin/bash folder='certs' keySize='1024' mv certs certs.old.$RANDOM &> /dev/null mkdir $folder mkdir $folder /trusted cd $folder openssl dhparam -outform PEM -out dh${keySize} .pem $keySize openssl req -x509 -nodes -newkey rsa:4096 -keyout ca.key -out ca.crt -days 3650 -subj "/C=GB/ST=London/L=London/O=Tunnel/OU=IT/CN=ufns" cat > extfile.txt <<EOF [ v3_req_p ] basicConstraints = CA:FALSE keyUsage = nonRepudiation, digitalSignature, keyEncipherment [ v3_ca_p ] basicConstraints = CA:TRUE keyUsage = nonRepudiation, digitalSignature, keyEncipherment, keyCertSign EOF openssl req -newkey rsa:4096 -nodes -keyout private.key -out certificate.csr -subj "/C=GB/ST=London/L=London/O=Tunnel/OU=IT/CN=xetg" openssl x509 -extfile extfile.txt -extensions v3_req_p -req -sha1 -days 3650 -CA ca.crt -CAkey ca.key -CAcreateserial -in certificate.csr -out certificate.crt mv ca.crt trusted
Now, after you copy/paste the code in SSF folder and run it. You get:
1 2 3 4 5 6 7 8 9 10 certs ├── ca.key ├── ca.srl ├── certificate.crt ├── certificate.csr ├── dh1024.pem ├── extfile.txt ├── private.key └── trusted └── ca.crt
Create SSF config file Create the file config.json in SSF folder
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 { "ssf": { "tls" : { "ca_cert_path": "./certs/trusted/ca.crt", "cert_path": "./certs/certificate.crt", "key_path": "./certs/private.key", "key_password": "", "dh_path": "./certs/dh1024.pem", "cipher_alg": "DHE-RSA-AES256-GCM-SHA384" }, "http_proxy" : { "host" : "127.0.0.1", "port" : 3128, "credential" : { "reuse_ntlm" : "false", "reuse_nego" : "false" } } } }
You need to configure the path of “keys” elements and cntlm proxy
Now it is is finish, you can copy/paste “certs” folder and config.jon on the remote host (VPS or whatever …) in SSF folder, and start the deamon
You can add “-v debug” to show more log.
On client side, in SSF folder, start the tunnel
1 ./ssf -D 1080 -p 443 [IP/Host]
If your configuration in OK you will get :
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 ./ssf -D 1080 -p 443 127.0.0.1 [config] loading file <config.json> [config] [tls] CA cert path: <file: ./certs/trusted/ca.crt> [config] [tls] cert path: <file: ./certs/certificate.crt> [config] [tls] key path: <file: ./certs/private.key> [config] [tls] key password: <> [config] [tls] dh path: <file: ./certs/dh1024.pem> [config] [tls] cipher suite: <DHE-RSA-AES256-GCM-SHA384> [config] [http proxy] <None> [config] [socks proxy] <None> [config] [circuit] <None> [ssf] connecting to <127.0.0.1:8011> [ssf] running (Ctrl + C to stop) [client] connection attempt 1/1 [client] connected to server [client] running [microservice] [stream_listener]: forward TCP connections from <127.0.0.1:1080> to 1080 [client] service <socks> OK
Now the socks tunnel is UP and listen on 127.0.0.1:1080.
If you need to have the ssfd running in background you can use screen .